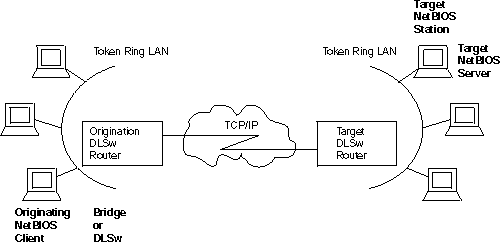

This chapter describes IBM's implementation of NetBIOS over bridged networks and over DLSw networks. It includes the following topics:
The NetBIOS protocol was designed for use on a Token-Ring LAN. It is not a routable protocol, but can be bridged, or switched using DLSw. Both of these methods of handling NetBIOS traffic are supported.
NetBIOS relies on broadcast frames for most of its functions other than data transfer. While this may not present a problem in LAN environments, if uncontrolled, it may easily present a problem in WAN environments.
The following sections describe NetBIOS names and the different types of NetBIOS broadcast communication.
The key to communication between NetBIOS stations are the NetBIOS names. Each NetBIOS entity is assigned a NetBIOS name. In order to communicate with another NetBIOS entity, its NetBIOS name must be known. The names are used in broadcast NetBIOS frames to indicate the source NetBIOS entity of the frame and the desired target NetBIOS entity to receive the frame.
All names in NetBIOS frames are 16 ASCII characters. There are two types of NetBIOS names:
This name is used to communicate with this particular NetBIOS entity.
This name is used to allow communication between a group of NetBIOS entities.
A single NetBIOS station (single MAC address) can have multiple individual and/or group names associated with it. These names are generated by the NetBIOS application based upon a name or names configured at the NetBIOS station by a network administrator.
When a NetBIOS entity is preparing to use an individual NetBIOS name as its own, it checks the network to make sure that no other NetBIOS station has already used this name.
It checks the NetBIOS name by repeatedly broadcasting a particular NetBIOS UI frame to all NetBIOS stations. If no stations respond, then the name is assumed to be unique and can be used. If a station does respond, the new station should not attempt to use this name.
To establish a NetBIOS session in order to do data transfer types of operations, the NetBIOS client first resolves the MAC address of the NetBIOS server and the LLC route to the NetBIOS server.
It does this by repeatedly broadcasting a particular NetBIOS UI frame to all NetBIOS stations. This frame contains the NetBIOS name of the server with which this client is establishing a session. When the server receives this frame with its NetBIOS name in it, the server responds with a corresponding broadcast NetBIOS UI frame to the client. When the client receives the response frame, the frame contains the MAC address and the route to the NetBIOS server.
For some NetBIOS applications, finding the NetBIOS server is a multiple step process. For example, the first step may be to find a domain controller that tells the client which domain server to use. Then the client finds this domain server.
Once the MAC address of NetBIOS server and the route to the NetBIOS server are found, the NetBIOS client can take either of the following actions:
For some NetBIOS applications, it is common to periodically broadcast data frames. This may be done if a station has a single frame's worth of data to send to another NetBIOS station. It can do this by broadcasting a particular NetBIOS UI frame (with the target NetBIOS station's name in the frame) to all NetBIOS stations.
Another case is when NetBIOS stations within a group (or domain) need to communicate with each other. This can be done by broadcasting a particular NetBIOS UI frame (with the target NetBIOS group name in the frame) to all NetBIOS stations. This is commonly done.
A less commonly used NetBIOS function is the ability to obtain status from any NetBIOS station. This is done by broadcasting a particular NetBIOS frame (with the target NetBIOS station's name in the frame) to all NetBIOS stations. When the target NetBIOS station receives this frame, it responds with a corresponding broadcast NetBIOS response frame.
There are two types of NetBIOS functions that are rarely used. Both of these functions involve broadcasting a NetBIOS frame to all NetBIOS stations. There is no target NetBIOS name in the frames. The two functions are:
To stabilize a network, the goal is to reduce the amount of broadcast NetBIOS traffic that is forwarded through the bridged or DLSw switched networks. This can be done in two ways:
Table 9 lists the filters that IBM provides.
| Filter Type | Filters |
|---|---|
| MAC Address | Frames by either the source or destination MAC address. |
| Byte | Frames by byte offset and field length within a frame. |
| Name | Frames by NetBIOS source and destination names. |
| Duplicate Frame | Duplicate frames. |
| Response | Responses for which the router did not forward a NetBIOS broadcast frame. |
Once the router filters frames, NetBIOS name lists and NetBIOS name caching and route caching controls how the remaining frames are forwarded. "NetBIOS Byte Filtering" and "NetBIOS host-name Filtering" describe byte and name filtering, respectively. The Software User's Guide describes MAC address filtering.
For an introduction to host-name filtering and byte filtering, see "NetBIOS Name and Byte Filters".
The following sections describe frame type, duplicate frame, response frame filtering, NetBIOS name lists, NetBIOS name and route caching.
Frame type filtering allows certain categories of NetBIOS frames to be filtered entirely for bridge traffic, DLSw traffic, or both DLSw and bridge traffic.
The three categories of NetBIOS frames that can be filtered are:
These are the broadcast NetBIOS frames used to make sure that a NetBIOS name to be used is unique in the network.
In NetBIOS networks, it is critical that the NetBIOS names of stations to which a NetBIOS session is established (typically the NetBIOS servers) be unique. It is also usually critical that the individual NetBIOS names of stations within the same group (or domain) be unique. But it is often not critical that the NetBIOS names of stations from which a NetBIOS session is setup (typically the NetBIOS clients) be unique, especially across domains.
For this reason, networks in which there is good control over the server names can gain advantage by filtering name conflict resolution frames. This is especially true for DLSw switched networks.
The NetBIOS name-conflict resolution frames are Add-Name-Query, Add-Group-Name-Query, and Add-Name-Response.
This is the broadcast NetBIOS frame used to send data to all NetBIOS stations in a network. This frame is rarely used and can typically be filtered.
The NetBIOS General Broadcast frame is Datagram-Broadcast.
These are the broadcast NetBIOS frames used to terminate NetBIOS traces in all NetBIOS stations in a network. These frames are rarely used and can typically be filtered.
The NetBIOS Terminate Trace frame is Terminate-Trace.
The default is to not filter any of the above frame types for bridged NetBIOS traffic, and to filter all of the above frame types for DLSw switched NetBIOS traffic. However, it may be advantageous to filter the above frame types if NetBIOS traffic is being bridged on WAN links.
For bridging, enter set filters bridge to turn frame type filtering on or off. For DLSw, enter set filters dlsw to turn frame type filtering on or off.
For example:
NetBIOS config>set filters bridge Filter Name Conflict frames? [Yes]: Name conflict filtering is ON Filter General Broadcast frames? [Yes]: General broadcast filtering is ON Filter Trace Control frames? [Yes]: Trace control filtering is ON
All of the broadcast NetBIOS frames that could have a response are sent a fixed number of times (default 6), at a fixed interval (default 1/2 second apart) by the origin NetBIOS station. In the following explanation, these frames are called NetBIOS command frames and the possible response frames are called NetBIOS response frames.
The NetBIOS command frames are the:
The command frames are sent multiple times to increase the odds of successful delivery (these frames are connectionless frames). Each response frame is sent only once in response to each command frame received.
In a DLSw-switched network, the forwarding of each retry across the WAN sessions can be very costly. So, when the first command frame is received, it is forwarded to the appropriate neighbor DLSw and bridge ports and a copy is saved. All retries of the same NetBIOS command frame received during a configurable time period are discarded.
There is one configurable time period for the bridge network and one configurable time period for the DLSw network.
The configurable time period for the bridge network is controlled by two commands:
If duplicate frame filtering is enabled for the bridge network, this value specifies for how long a period to discard duplicate NetBIOS command frames after a NetBIOS command frame has been bridged.
If a duplicate NetBIOS command frame is received after the timeout expires, the frame is forwarded to the bridge network.
The configurable time period for the DLSw network is controlled by a single parameter:
This value specifies for how long a period to discard duplicate NetBIOS command frames after a NetBIOS command frame has been forwarded to the DLSw network.
If a duplicate NetBIOS command frame is received after the timeout expires, the frame is forwarded to the DLSw network.
| Note: | Filtering of duplicate NetBIOS command frames to a DLSw network is always enabled. |
When a NetBIOS command frame is received by a DLSw neighbor, the frame is forwarded to the bridge network and a copy is saved. At a configurable interval (1/2 second) for a configurable number of times (default 6), the neighbor DLSw function forwards a retry of the command frame to the bridge function. The bridge function handles the command frame based upon the configured bridge duplicate frame parameters.
The configurable number of retries and interval are controlled by the following command and parameters:
There is one last parameter that controls how long the command frame is saved in order to perform the above bridge and DLSw network forwarding:
This parameter indicates how long a received NetBIOS command frame is saved for duplicate frame and response frame processing. After the timeout expires, the command frame is deleted and the duplicate frame filter timer and reduced search timer associated with it are cancelled. The first duplicate command frame received after the timeout period is treated as the first command frame received. All response frames received after the timeout period are discarded.
Figure 24. Setting Up a NetBIOS Session Over DLSw. Duplicate filtering reduces the number of broadcast frames forwarded over the DLSw WAN.

Figure 24, together with the following sequence, shows how the process works, using the default values. To simplify things, it is assumed that no response frame is received.
Origin Originating Target Target
NB stn Router Router NB stn
Bridge DLSw DLSw Bridge
BEGIN
TIME NB cmd frame (1) NB cmd frame (1)
*-----------------*-to dlsw--------------------------------------->
* <--to bridge *--*
0.5 sec. .5 second (origin NB stn timer) .5 second (command frame retry timer)
|
|
| NB cmd frame (2) NB cmd frame (2)
| *--------> *------* *----------------->
* <--to bridge *--*
1 sec. .5 second (origin NB stn timer) .5 second (command frame retry timer)
*
|
| NB cmd frame (3) NB cmd frame (3)
| *--------> *------* *----------------->
| <--to bridge *--*
1.5 sec. .5 second (origin NB stn timer) .5 second (command frame retry timer)
| (reduced search timer)
|
|
| NB cmd frame (4) NB cmd frame (4)
| *-----------------*-to dlsw--------------------------------------->
* <--to bridge *--*
2 sec. .5 second (origin NB stn timer) .5 second (command frame retry timer)
*
|
| NB cmd frame (5) NB cmd frame (5)
| *--------> *------* *----------------->
| <--to bridge *--*
2.5 sec. .5 second (origin NB stn timer) .5 second (command frame retry timer)
|
|
| NB cmd frame (6) NB cmd frame (6)
| *--------> *------* *----------------->
| <--to bridge *--*
*
5.0 sec. 2.5 seconds (dup frame detect timer) 2.5 seconds (dup frame detect timer)
deleted NB cmd frame deleted NB cmd frame
|
The sequence of events is as follows:
The NetBIOS session setup command frame and the NetBIOS status command frame each expect a corresponding NetBIOS response frame. If no response frame is received, the command frame is retried as in the example above.
When the first NetBIOS response frame is received on the bridge network at the target router, it is forwarded back to the origin router and the saved NetBIOS command frame is deleted. Any subsequent response frame received at the target router is discarded because no corresponding NetBIOS command frame is found.
At the origin router, the received response frame is forwarded on the bridge network and the saved NetBIOS command frame is deleted. Any subsequent response frames received at the origin router (from the DLSw or bridge network) are discarded.
The NetBIOS name conflict command frames may cause, but do not require, a corresponding NetBIOS response frame. In addition, all received response frames are used (to determine whether there is more than one conflict).
Therefore, all NetBIOS name conflict frames received are forwarded, but the NetBIOS command frame is not deleted until the Duplicate Frame Detect timer expires.
NetBIOS name lists is a DLSw-only vehicle for limiting the number of DLSw partners to which a NetBIOS UI frame is forwarded.
A local NetBIOS name list can be configured at each router. This name list represents all of the NetBIOS names attached to the router's locally bridged network that can be accessed by DLSw partners. The router sends the local NetBIOS name list to all DLSw partners. These partners use the list to limit the NetBIOS traffic the partner sends to this router.
The NetBIOS name lists are useful in environments in which there is good control over the NetBIOS names; particularly those environments that should be accessed remotely through DLSw.
A NetBIOS name list is a set of NetBIOS name list entries. Configuring of the local NetBIOS name list involves:
You configure the name list entries at the NetBIOS config> prompt with the add name-list command. Each entry consists of the following information:
The ? (question mark) signifies that the character in that position in the NetBIOS name may have any value.
The * (asterisk) as the last character of a name to signifies that all of the remaining characters in the NetBIOS name may be any value.
| Note: | In the majority of client/server NetBIOS applications, the only names required in the name lists are those of servers or domains. Individual client names do not need to be configured in name lists. |
As a general rule, domain names are group names and client or server names are individual names.
The name list itself has an attribute that is configured at the NetBIOS config> prompt using the SET NAME-LIST command. That attribute is name list exclusivity.
The attribute indicates whether the set of name list entries represents all NetBIOS names that this router's DLSw partners can reach (exclusive) or represents some but not necessarily all NetBIOS names that this router's DLSw partners can reach (non-exclusive).
An exclusive name list does the best job of limiting NetBIOS DLSw traffic on the network. Only frames destined to a NetBIOS name represented by a router's exclusive name list are forwarded to that router.
A non-exclusive name list helps limit NetBIOS DLSw traffic on the network though not as well as an exclusive name list. Frames destined to a NetBIOS name represented by a router's non-exclusive name list will be forwarded to that router first.
If the router receives a frame destined to a NetBIOS name not represented by any router's name lists, the router forwards the frame to all routers with non-exclusive name lists.
It is possible to control how a particular router uses its local NetBIOS name list and the name lists received from its DLSw partners using the following parameters:
If you enable use local NetBIOS name list, the router sends the local NetBIOS name list configured at the router to all DLSw partners.
If you disable use local NetBIOS name list, the router does not send the local NetBIOS name list configured at the router to all DLSw partners.
If you enable use remote NetBIOS name lists, the router uses all NetBIOS names lists received from the router's DLSw partners to determine how to forward certain NetBIOS frames.
If you disable use remote NetBIOS name lists, the router ignores all NetBIOS name lists received from the router's DLSw partners.
You can change all the NetBIOS name list parameters either permanently at the NetBIOS config> prompt or temporarily at the NetBIOS> prompt.
Because each change made requires the router to send information to each DLSw partner, you must indicate that the name list changes are ready for use by entering set name-list at the NetBIOS> command prompt.
The router uses NetBIOS name lists to determine how to forward the following NetBIOS frames:
Configure exclusive NetBIOS name lists whenever possible. If you configure and send an exclusive name list to all DLSw partners, then the only NetBIOS frames received from the DLSw partners will be the frames whose destination name matches one of the name list entries.
A useful exclusive NetBIOS name list is the empty NetBIOS name list. If a particular router has no NetBIOS servers that are to be accessed by any of its DLSw partners, you should use an empty exclusive name list.
If a router has many DLSw partners all on different bridged networks, you can use non-exclusive name lists. Name list entries could be configured for the most frequently used servers so that traffic destined for these servers would go to this router first. Specifying the name list as non-exclusive allows traffic to go to less frequently used servers without having to configure the servers in the name list. Use this configuration in a network without tight control of the NetBIOS names; particularly the servers to be accessed remotely through DLSw.
Another use of non-exclusive NetBIOS name lists is in configurations that contain parallel DLSw paths between bridged networks. If two routers are on the same bridged network, one router could configure a NetBIOS name list representing one set of servers to be accessed remotely through DLSw on the bridged network and the other router could configure a NetBIOS name list representing a different set of servers. When both routers are active, the NetBIOS traffic is distributed between the two routers. If one router is inactive, all NetBIOS traffic will go through the other router because it has a non-exclusive list.
The default name list is an empty non-exclusive NetBIOS name list. This indicates that a router wants its DLSw partners to send all unforwardable NetBIOS traffic to the router.
NetBIOS Name Caching is the function in the router that classifies the type of NetBIOS name and the information necessary to reach the NetBIOS name. This information is used to best determine how to forward unfiltered NetBIOS frames to as few DLSw neighbors and as few bridge ports as possible. The possible types of NetBIOS names and the information saved for each are:
Whenever NetBIOS session setup frames or connectionless data transfer frames are received, the name cache is used to determine how to forward the frame. If one of these frames is received on the bridge network at a router, one of the following actions is taken:
If matches with group name qualifiers are found, a NetBIOS name cache entry is created with the name type group. The frame is forwarded on all bridge ports and to all DLSw partners with non-exclusive name lists or exclusive name lists with a matching name list entry.
If matches with individual name qualifiers are found, a NetBIOS name cache entry is created with the name type individual remote. The frame is forwarded to each DLSw partner with a matching name list entry.
If no matches are found, a NetBIOS name cache entry is created with the name type unknown. The frame is forwarded on all bridge ports and to all DLSw partners with non-exclusive name lists.
If multiple equally best TCP sessions are learned, they will be used alternately on different NetBIOS session setup frames.
If route caching is disabled, the NetBIOS frame's routing information is left alone, and the frame is forwarded to all bridge ports.
If route caching is enabled, the NetBIOS frame's routing information is updated with the saved routing information and the frame is forwarded to the proper bridge port (determined by the MAC address and route).
NetBIOS names are learned and classified from information in the NetBIOS session setup frames (Name-Query and Name-Recognized).
It is possible to configure individual remote NetBIOS names and associate them with a particular DLSw TCP session. This can greatly reduce the search overhead. To improve performance, it is recommended to configure the remote NetBIOS servers that are accessed commonly by NetBIOS clients in the router's local bridge network.
It is not possible to configure individual local NetBIOS names and associate them with a particular MAC address and route.
There are three types of NetBIOS name cache entries:
Enter add cache-entry at the NetBIOS config> prompt to add a permanent entry. You are prompted to enter the NetBIOS name and the associated IP address.
Enter add cache-entry at the NetBIOS> console prompt to add a static entry. You are prompted to enter the NetBIOS name and the associated IP address.
To prevent one type of NetBIOS name from filling up the entire name cache, there are two configurable NetBIOS name cache limits:
If an entry is not referenced for a configurable timeout period, then it is automatically deleted. This timeout out period is the unreferenced entry timeout value.
The association of a NetBIOS name with either a TCP session or a MAC address and route is made at one instance in time. Because networks are changing and the best path to a NetBIOS name may change, the association between a NetBIOS name and a TCP session or a MAC address and route is saved for only a configurable period of time. After this period of time, a new best path association is learned. The parameter that controls this configurable period of time is the best path aging timeout value.
Another useful configuration parameter is the reduced search timeout value. In addition to controlling for what period of time duplicate command frames are filtered to the DLSw network, it also controls how long to wait before expanding the search for a NetBIOS name. If a NetBIOS session setup frame is received and the destination NetBIOS name is found in the router's NetBIOS name cache as an individual remote frame, then the frame is forwarded to the corresponding TCP session. If no response to this frame is received, it could be due to the name no longer being accessible via this path. The first duplicate NetBIOS session setup frame received after the reduced search timer expires is forwarded to all DLSw TCP sessions, thus expanding the search to look for a better path.
The last parameter, significant characters in name, controls how many of the 16 characters in a NetBIOS name are needed to consider it a unique NetBIOS name. Some NetBIOS applications use the 16th character of the NetBIOS name to distinguish between certain entities associated with a single NetBIOS name (for example, print server and file server). In these cases, it is best to specify significant characters in name as 15. This causes any frame in which the first 15 characters of the destination NetBIOS name matches the first 15 characters of the router's NetBIOS name cache entry to be forwarded according to the name cache entry information. Thus multiple NetBIOS names can be represented with a single NetBIOS name cache entry.
All of the above NetBIOS name cache related parameters can be configured using the set cache-parms command as follows.
NetBIOS config>set cache-parms Significant characters in name [15]? Best path aging timeout value in seconds [60.0]? Reduced search timeout value in seconds [1.5]? Unreferenced entry timeout value in minutes [5000]? Max nbr local name cache entries [500]? Max nbr remote name cache entries [100]? Cache parameters set
See "NetBIOS Commands" for more information on the set cache-parms command.
The router provides the following commands that let you view cache
entries. From the NetBIOS configuration prompt, you can use the
list cache commands in Table 10.
Table 10. NetBIOS List Cache Configuration Commands
| Command | Displays . . . |
|---|---|
| list cache all | All permanent entries. Does not show static and dynamic entries. |
| list cache entry-number | A permanent cache entry according to its entry number. |
| list cache NetBIOS-name | A permanent cache entry for a specific NetBIOS name. |
| list cache ip-address | A permanent cache entry for a specific IP address. |
From the NetBIOS monitoring prompt, you can use the list cache commands in Table 11.
Table 11. NetBIOS List Cache Monitoring Commands
| Command | Displays . . . |
|---|---|
| list cache active | All active entries in the router's name cache, including permanent, static, and dynamic entries. |
| list cache config | Static and permanent entries. Does not show dynamic entries. |
| list cache group | Entries that exist for NetBIOS group names. |
| list cache local | Local cache entries. Local cache entries are those that the router learns over the bridged network. |
| list cache name | A cache entry for a specific NetBIOS name. |
| list cache remote | Remote cache entries. These are entries that the router learns over the DLSw WAN. |
| list cache unknown | Entries where the type of NetBIOS entry is unknown. The router considers all entries unknown until it learns the type of entry. |
The following sections provide examples of how to set up NetBIOS filtering. The first explains how to create a host-name filter. The second demonstrates how to configure a byte filter. For more information on the commands used in these examples, see "NetBIOS Commands".
To create a host-name filter, enter commands at the NetBIOS Filter config> prompt.
Config>protocol asrt Adaptive Source Routing Transparent Bridge user configuration ASRT config>NetBIOS NetBIOS Support User Configuration NetBIOS config>set filter name NetBIOS Filtering configuration NetBIOS Filter config>
Use the following procedure to create a host-name filter.
NetBIOS Filter config>create name-filter-list Handle for Name Filter List []? boston
Enter update to get to the prompt for that specific filter list. From this prompt, you can add filter items to the filter list.
NetBIOS Filter config>update Handle for Filter List []? boston Name Filter List Configuration NetBIOS Name boston config>
| Note: | This entry is case sensitive. |
The following example adds a filter item to the host-name filter list boston, which allows packets containing the hostname westboro (an ASCII string) to be bridged (configured as inclusive). No <LAST-hex-number> parameter has been configured for this entry.
NetBIOS Name boston config>add inclusive ascii Hostname []? westboro Special 16th character in ASCII hex (<CR> for no special char) []?
You can enter all parameters as one string on the command line if you do not want to be prompted. Be sure to use a space between each parameter.
Type list to verify your entry:
NetBIOS Name boston config>list NAME Filter List Name: boston NAME Filter List Default: Inclusive Item # Type Inc/Ex Hostname Last Char 1 ASCII Inc westboro
Repeat the first four steps to add additional filter items to the filter list. The order in which you enter filter items is important because this determines how the router applies the filter items to a packet. The first match stops the application of filter items and the router either forwards or drops the packet, depending on whether the filter item is Inclusive or Exclusive.
Entering the most common filter items first makes the filtering process more efficient because the software is more likely to make a match at the beginning of the list.
If the packet does not match any of the filter items, the router uses the default condition (Inclusive or Exclusive) of the filter list. You can change the default condition of the list by entering default inclusive or default exclusive at the filter list configuration prompt. For example:
NetBIOS Name boston config> default exclusive
NetBIOS Name boston config>exit NetBIOS Filter config>
The filter list containing the filter items can now be added as a filter to your bridging router configuration. Use the filter-on command to do this. Configure host-name filters with the following parameters (entered in this order):
The following example adds a host-name filter to affect packets input on port #3. It is comprised of the host-name filter list boston. All packets input on port #3 are evaluated according to the rules provided by the filter items contained in the filter list boston. This means that all packets input on port #3 containing the hostname westboro are bridged.
NetBIOS Filter config>filter-on input Port Number [1]? 3 Filter List []? boston
Enter list to verify your entry:
NetBIOS Filter config>list
NetBIOS Filtering: Disabled
NetBIOS Filter Lists
--------------------
Handle Type
nlist Name
newyork Name
HELLO Byte
boston Name
NetBIOS Filters
---------------
Port # Direction Filter List Handle(s)
3 Output nlist
1 Input newyork OR HELLO
3 Input boston
Use the enable command to globally enable NetBIOS filtering on the router.
NetBIOS Filter config>enable NetBIOS-filtering
Enter exit followed by Ctrl-P to return to the * prompt. From this prompt, enter restart to activate all software changes made during the NetBIOS filtering configuration process.
NetBIOS Filter config>exit ASRT config>exit Config> Ctrl-P * restart
Use the following procedure as a guideline for creating a byte filter. Enter all commands at the NetBIOS filtering config> prompt.
Config>protocol asrt Adaptive Source Routing Transparent Bridge user configuration ASRT config>NetBIOS NetBIOS Support User Configuration NetBIOS config> set filter byte NetBIOS Filtering configuration NetBIOS Filter config>
NetBIOS Filter config>create byte-filter-list Handle for Byte Filter List []? westport
Enter update to get to the prompt for that specific filter list. From this prompt you can add filter items to the filter list.
NetBIOS Filter config>update Handle for Filter List []? westport Byte Filter List Configuration NetBIOS Byte westport config>
Begin adding filter items to the filter list with the add command. The way filter items are configured determines which NetBIOS packets are bridged or dropped. Byte filter items are configured with the following parameters (entered in this order):
The following example adds a filter item to the Byte filter list westboro that allows packets with a hex pattern 0x12345678 at byte offset of 0 to be bridged (configured as inclusive). No hex mask is present.
NetBIOS Byte westport config>add inclusive Byte Offset [0]? 0 Hex Pattern []? 12345678 Hex Mask (<CR> for no mask) []?
NetBIOS Byte westport config>list BYTE Filter List Name: westport BYTE Filter List Default: Inclusive Item # Inc/Ex Offset Pattern Mask 1 Inc 0 0x12345678 0xFFFFFFFF
Repeat the first three steps to add additional filter items to the filter list.
NetBIOS Byte westport config>exit NetBIOS Filter config>
The order in which you enter filter items is important, because this determines how the router applies the filter to a packet. The first match stops the application of filter items and the router either forwards or drops the packet, depending on whether the filter item is Inclusive or Exclusive.
Entering the most common filter items first makes the filtering process more efficient because the software is more likely to make a match at the beginning of the list rather than having to check the whole list before making a match.
If the packet does not match any of the filter items, the router uses the default condition (Inclusive or Exclusive) of the filter list. You can change the default condition of the list by entering default inclusive or default exclusive at the filter list configuration prompt. For example:
NetBIOS Byte westport config> default exclusive
The filter list containing the filter items can now be added as a filter to your bridging router configuration. Use the filter-on command to do this. Configure host-name filters with the following parameters (entered in this order):
The following example adds a host-name filter to affect packets output on port #3. It is comprised of the byte filter list westboro. All packets output on port #3 will be evaluated according to the rules provided by the filter items contained in the filter list westboro.
NetBIOS Filter config>filter-on output Port Number [1]? 3 Filter List []? westboro
Enter list to verify your entry:
NetBIOS Filter config>list
NetBIOS Filtering: Disabled
NetBIOS Filter Lists
-------------------
Handle Type
nlist Name
newyork Name
HELLO Byte
westboro Byte
NetBIOS Filters
---------------
Port # Direction Filter List Handle(s)
3 Output nlist
1 Input newyork OR HELLO
3 Output westboro
Enter enable to globally enable NetBIOS filtering on the bridging router.
NetBIOS Filter config>enable NetBIOS-filtering
Enter exit followed by Ctrl-P to return to the * prompt. Enter restart.
NetBIOS Filter config>exit ASRT config>exit Config> Ctrl-P * restart